Is it truly possible to unlock the potential of your Raspberry Pi from any corner of the globe, without emptying your wallet? Absolutely. Remote access to your Raspberry Pi, a gateway to endless possibilities, is not only feasible but surprisingly accessible, and the best part is it can be achieved entirely free of charge.
The allure of being able to command your compact computer from afar is undeniable. Imagine the convenience of managing your projects, accessing crucial files, or even troubleshooting issues, all without the need to physically be present. Setting up remote access for your Raspberry Pi, hidden behind the protective shield of your home router, is a skill rapidly becoming indispensable for a diverse audience from the eager hobbyist and the tech-savvy enthusiast to the seasoned professional. In this exploration, we delve into the straightforward methods that empower you to transform your Raspberry Pi into a truly global asset.
Let's consider the practical implications. Perhaps you're a student working on a coding project, or a home automation enthusiast monitoring your smart devices. Maybe you're a professional managing a small server. In each of these scenarios, the ability to remotely access your Raspberry Pi offers unparalleled flexibility and control. The days of being tethered to your local network are over. Now, your Raspberry Pi is as accessible as your internet connection.
Let's consider the hypothetical example of a user named Alex, a software developer with a passion for home automation projects, utilizing remote access. To illustrate the concept, we'll construct a profile based on Alex and his experiences, providing a framework for the implementation of remote access to a Raspberry Pi.
| Category | Details |
|---|---|
| Full Name | Alex Johnson |
| Age | 32 |
| Location | San Francisco, CA |
| Education | Bachelor of Science in Computer Science, Stanford University |
| Career | Software Developer, specializing in IoT and embedded systems |
| Professional Skills | Proficient in Python, C++, Linux administration, network configuration, and Raspberry Pi programming |
| Raspberry Pi Projects | Home automation system, weather station, and a personal media server |
| Remote Access Goals | To monitor and control home automation devices, access media files, and manage software deployments from any location. |
| Tools and Technologies | Raspberry Pi 4 Model B, Router with Port Forwarding Capabilities, SSH, and a dynamic DNS service (e.g., No-IP) |
| Reference Website | Raspberry Pi Foundation |
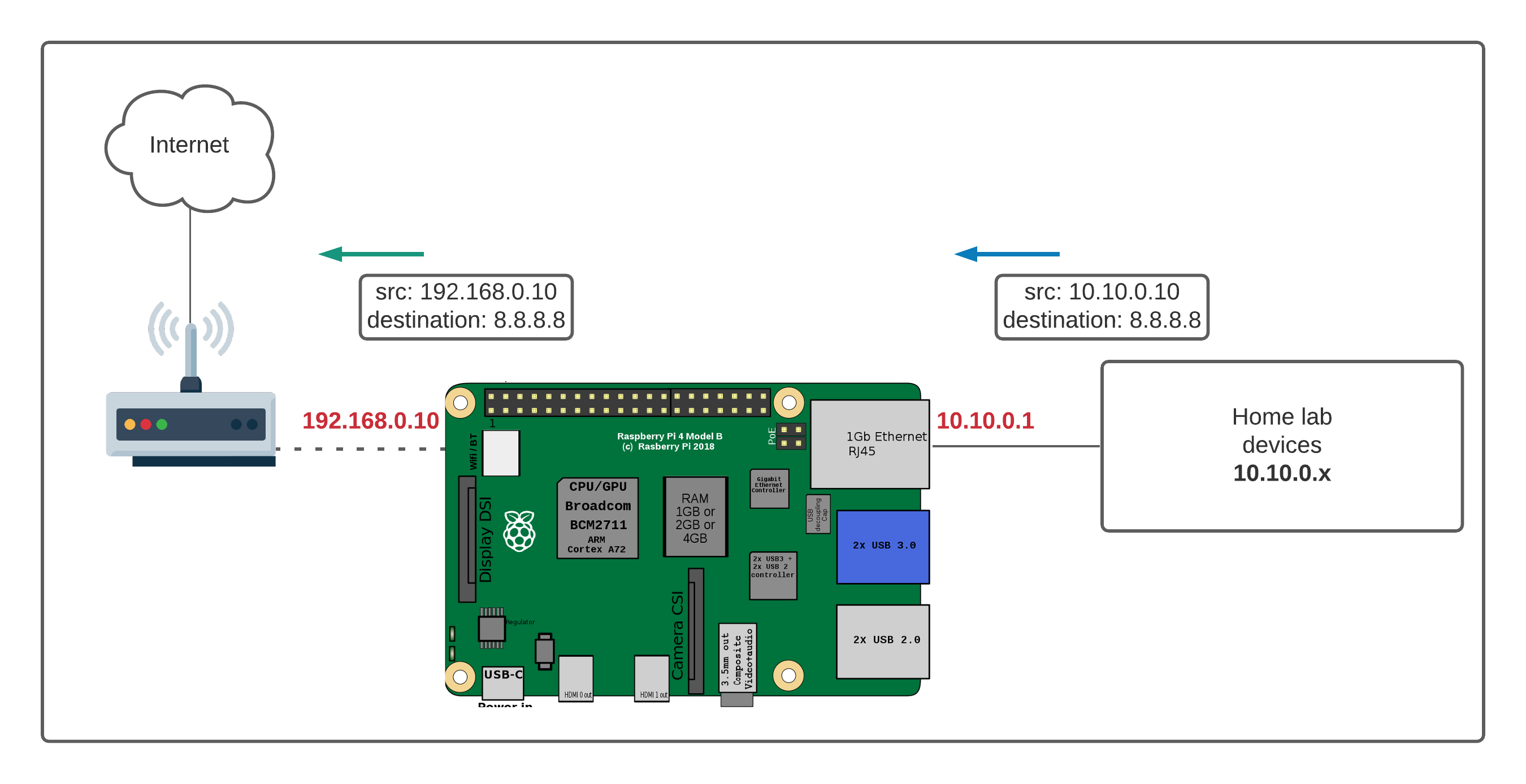
Let's now discuss the technical underpinnings and various approaches. The fundamental principle involves configuring your router to allow external access to your Raspberry Pi. This usually involves a process called port forwarding. However, there are simpler methods also. The following discussion outlines some key points:
The primary goal is to establish a secure and reliable connection from outside your local network to your Raspberry Pi. The challenge is that your home network's public IP address can change. This is where Dynamic DNS services come into play.
Port Forwarding
This is a fundamental technique. Your router acts as a gatekeeper. You configure it to forward specific incoming traffic on certain ports to the Raspberry Pi's local IP address. The most common port used for SSH is port 22, though you can change this for added security. By forwarding port 22 to your Raspberry Pi's internal IP address, you are essentially telling your router to direct any incoming SSH requests to your Pi.
Dynamic DNS (DDNS)
Home internet connections typically receive dynamic IP addresses from their internet service provider (ISP). These addresses change periodically. A Dynamic DNS service solves this problem. It provides a static hostname (e.g., myraspberrypi.example.com) that automatically updates its IP address to match your changing public IP address. This way, you can always access your Raspberry Pi using the same easy-to-remember hostname, regardless of your changing IP address.
SSH (Secure Shell)
SSH is a secure network protocol used for remote login and other secure network services. When you connect to your Raspberry Pi via SSH, all communication is encrypted, protecting your data from eavesdropping. Once connected, you can access the command line interface, access files, and run programs on the Pi.
Setting Up Port Forwarding: A Practical Guide
The exact steps will vary slightly depending on your router's make and model. Generally, you'll need to access your router's configuration interface by typing its IP address (usually 192.168.1.1 or 192.168.0.1, but check your router's documentation) into your web browser. You'll then log in using your router's administrative username and password. Find the "Port Forwarding" or "Virtual Server" settings. Create a new rule. Specify the port to forward (e.g., 22 for SSH). Enter the local IP address of your Raspberry Pi. Save the settings, and you're done.
Configuring Dynamic DNS
Sign up for a free Dynamic DNS service (e.g., No-IP, DynDNS). Create a hostname for your Raspberry Pi (e.g., myraspberrypi.ddns.net). Download and install a DDNS client on your Raspberry Pi. This client will automatically update your hostname's IP address whenever it changes. The installation process is quite simple and often involves downloading a package using `apt` or a similar package manager and then following a series of prompts to configure your DDNS account credentials.
SSH Key-Based Authentication: Enhancing Security
While password authentication is the default, it is not the most secure. Implement SSH key-based authentication. This involves generating a public/private key pair. You copy the public key to your Raspberry Pi. When you try to connect, you'll use your private key to authenticate. The advantage is much better security, and often ease of use. Furthermore, it reduces the risk of brute-force attacks targeting your password.
Firewall Configuration on the Raspberry Pi
While port forwarding opens a specific pathway, you also want to protect your Raspberry Pi's services. Employing a firewall such as `ufw` (Uncomplicated Firewall) helps. You can configure it to permit incoming SSH traffic only from specific IP addresses (for enhanced security). You can allow outgoing connections as well, by default. For example, you would type something like: `sudo ufw allow ssh` to permit ssh connections. It is generally considered a good practice to enable the firewall by default: `sudo ufw enable`
Beyond the Basics: Advanced Techniques
Setting up a VPN (Virtual Private Network)
For enhanced security and privacy, consider setting up a VPN on your Raspberry Pi. A VPN creates an encrypted tunnel between your device and your home network. This protects all your traffic, not just SSH connections. There are various VPN server software packages available, such as OpenVPN, and WireGuard. Installation usually requires a series of command-line steps, including the generation of key pairs and certificate authority files, which can then be used to secure your private tunnel.
Using Reverse SSH Tunnels
If you are behind a restrictive firewall that blocks incoming connections, or if you're on a network where you can't configure port forwarding, a reverse SSH tunnel might be your solution. The Raspberry Pi initiates a connection to a server you control (often a VPS Virtual Private Server), creating an outgoing SSH connection. You can then connect to that server, which then forwards traffic to your Raspberry Pi.
Securing Your Raspberry Pi: Best Practices
The steps to secure your device are vital, and should be followed.
Change the Default Password: The first thing you should do is change the default username and password. Keep Your Software Updated: Use `sudo apt update` and `sudo apt upgrade` regularly to install security patches. Disable Unnecessary Services: Disable any services on your Raspberry Pi that you don't need to reduce the attack surface. Use a Strong Password: If using password authentication (even with key-based authentication), use a strong, unique password. Monitor Your Logs: Regularly review your system logs (e.g., `/var/log/auth.log`) for suspicious activity. Limit Login Attempts: Configure your SSH server to limit the number of failed login attempts before locking the user account.
Troubleshooting Common Issues
Connection Refused: This typically indicates that the SSH service is not running on your Raspberry Pi, the port forwarding is not configured correctly, or the firewall is blocking the connection. Cannot Resolve Hostname: This suggests an issue with your Dynamic DNS configuration, or that the hostname cannot be resolved to an IP address at the time of the connection attempt. Connection Timed Out: This may suggest issues with the network connectivity (the Pi is not connected to the internet), the router settings, or the firewall.
Practical Examples and Use Cases
Alex, the software developer, can use his remote access setup to do the following:
Manage his home automation system: He can check the status of his smart lights, adjust the thermostat, and monitor security cameras, all from his mobile phone. This gives him peace of mind, especially while he's away from home. Access his media server: He can access his personal media library, play movies and music, and manage his files, regardless of his location. He effectively has his own personal streaming service that can be managed on-the-go. Deploy software updates: He can remotely deploy and test software updates to his Raspberry Pi-based projects without having to physically interact with the device.
Remote Access for Educational Purposes
For students, remote access facilitates the continuation of coding projects or experimenting with Raspberry Pi hardware, even when they don't have physical access to their setup.
The Future of Remote Access
As technology continues to advance, the methods for remote access are also evolving. The convenience and security aspects will continue to improve, driven by more sophisticated services and protocols. Furthermore, we should expect to see the role of the Raspberry Pi expand, with the rise of edge computing, and more. Raspberry Pi will become even more prevalent in the tech world.
The ability to remotely access your Raspberry Pi from anywhere is a powerful asset, but the ability to do so without spending a dime is an amazing advantage. The methods outlined in this guide provide the building blocks for a secure and accessible remote connection to your Raspberry Pi. From the simple elegance of SSH to the added security of key-based authentication and the encompassing protection of a VPN, you have the tools to take control of your device, access your files, and manage your projects from anywhere in the world. The interconnected world is at your fingertips; all you need is your Raspberry Pi and an internet connection.