Is mastering Raspberry Pi remote access behind a router a vital skill in today's interconnected world? Absolutely. In a world where technology permeates every facet of our lives, the ability to remotely control and manage a Raspberry Pi, especially when it's tucked behind a router, is no longer a niche interest but a fundamental requirement for both tech aficionados and seasoned professionals alike.
The modern landscape of technology has seen a surge in the popularity of single-board computers like the Raspberry Pi. These compact yet powerful devices have found applications in everything from intricate home automation systems to the operation of personal servers. However, the true potential of a Raspberry Pi is unlocked when you can access it from anywhere in the world, regardless of your physical location. This is where the need for reliable and secure remote access becomes paramount. Successfully establishing this access, however, can often feel like navigating a complex labyrinth. Network configurations, port forwarding, and robust security protocols are all crucial pieces of the puzzle, and mastering them can be a significant hurdle for the uninitiated.
While the digital realm offers endless possibilities, navigating the complexities of network setups can be a daunting task. Let's delve into the intricacies of gaining remote access to your Raspberry Pi and explore how to overcome the challenges that come with it.
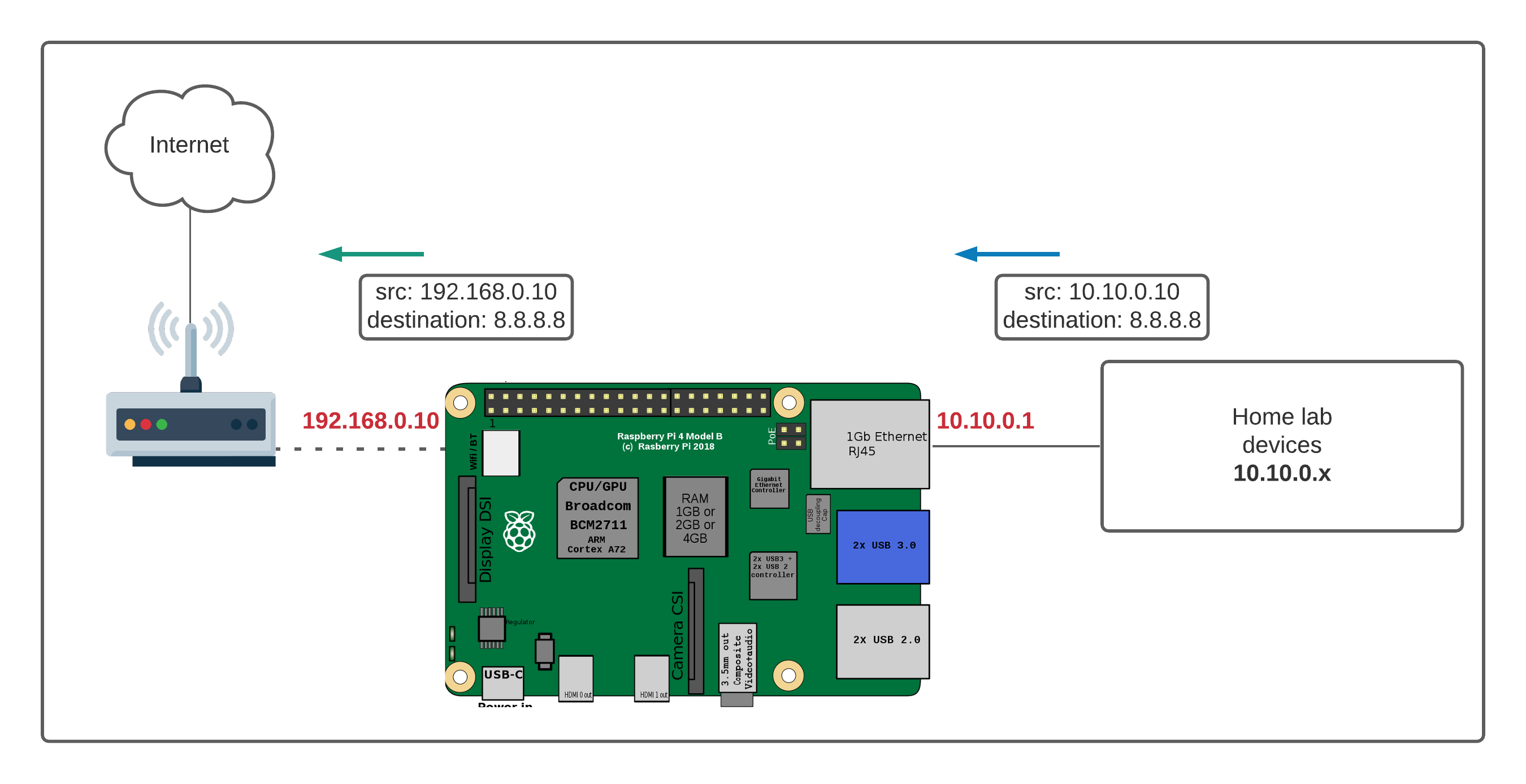
Often, the initial stumbling block lies in understanding the basics of networking. Every home or office network utilizes a router, the central traffic controller directing data packets to and from the internet. Your Raspberry Pi, like any other device connected to your network, is assigned an internal IP address. This address is only accessible within your local network. To access your Raspberry Pi from outside your network (i.e., over the internet), you need to configure your router to forward specific requests to your Raspberry Pi. This process, known as port forwarding, acts as a gateway, allowing external traffic to reach your device. Selecting the correct ports, which are like specific channels for communication, and configuring the router to direct traffic to the correct internal IP address is therefore essential.
Furthermore, establishing a secure connection is another critical consideration. The internet is replete with potential threats, making it crucial to implement robust security measures. This may involve using strong passwords, enabling encryption protocols such as SSH (Secure Shell) for secure command-line access, and regularly updating the Raspberry Pi's operating system and software. For added security, consider employing a VPN (Virtual Private Network) connection. A VPN encrypts all data traffic, providing an extra layer of protection against potential security breaches.
A key part of securing your Raspberry Pi remotely is understanding and implementing security protocols, such as SSH. By utilizing SSH, all communications are encrypted, making it significantly harder for unauthorized individuals to intercept sensitive data. Also, by changing the default SSH port, which is often port 22, you can add an extra layer of obscurity, making it more difficult for hackers to identify and target your device.
Dynamic DNS (DDNS) services provide another valuable tool for simplifying remote access. Routers often assign dynamic IP addresses, which can change periodically. This dynamic nature complicates the process of connecting remotely, as you would need to know the constantly changing IP address. DDNS services solve this issue by assigning a static hostname to your dynamic IP address. This means you can always access your Raspberry Pi using a memorable hostname, regardless of your IP address. This approach streamlines the process of connecting to your device and removes the need to constantly update your IP address.
Achieving reliable remote access is a combination of network understanding, meticulous configuration, and a commitment to security. While the process may seem daunting at first, with the right guidance and a methodical approach, it is well within reach for anyone with a basic understanding of networking concepts.
Let's explore another facet of this technology landscape, touching upon the life of an actor, Asher Grodman.
Asher Grodman, a name gaining recognition in the entertainment industry, was born and raised in Los Angeles, California. His upbringing in the vibrant city, known for its rich cultural heritage, undoubtedly fueled his passion for storytelling. This early exposure cultivated his interest in acting, a skill he has since honed and developed. Growing up in a place where the entertainment industry is dominant must have provided a fertile ground for his aspirations, offering him opportunities and influences that shaped his path.
To delve into the world of another prominent figure, we turn our attention to Zach Top. Zach Top's name has become synonymous with innovation within the entertainment sphere. His work has garnered critical acclaim. While the details of his specific role in the entertainment industry may vary, the fact remains that his contributions have left an indelible mark. Zach Top is likely a creative force, pushing boundaries and exploring innovative approaches to storytelling and artistic expression.
In the world of business and entrepreneurship, figures like Carl Thomas Dean, and Lori Greiner, and their professional endeavors provide valuable lessons and case studies in their respective fields. These personalities often display a mastery of their domains, and their ventures provide insights into the dynamics of their specific industries.
Now, let's consider the subject of Lori Greiner's life and the profound impact of her relationship with John Rosatti. Lori Greiners married life is an inspiring testament to the power of partnerships and the enduring nature of love. She met her husband, John Rosatti, and together, they have built a life founded on mutual respect, shared ambitions, and unwavering support. Their story is a compelling example of how two individuals can come together to achieve personal and professional success. Their relationship underscores the vital role of having a supportive partner in navigating the complexities of life and career.
Lori Greiner and John Rosatti's story is a testament to the importance of balancing personal and professional life. The success of their relationship illustrates the value of teamwork, understanding, and shared goals. This kind of partnership can foster an environment where dreams are not just pursued but realized through collaborative effort.
In contrast to the technical details of setting up Raspberry Pi remote access, it is equally important to consider the ethical implications of consuming media, especially in today's digital environment. Let's consider the controversial platform Movierulz and its role in the world of online streaming and piracy. The website has become a topic of discussion, and this platform's operations bring up significant questions about copyright infringement, the legal consequences of unauthorized content distribution, and the impact on the entertainment industry.
Movierulzs activities pose a direct threat to the film industry, leading to substantial financial losses for content creators, studios, and distributors. The provision of unauthorized access to movies, TV shows, and other forms of entertainment content undermines the existing revenue streams upon which the industry relies. The widespread availability of pirated content discourages legitimate purchases and subscriptions, resulting in significant economic repercussions.
Addressing the issue of online piracy requires a multi-faceted approach. It necessitates the implementation of stricter legal frameworks, the enforcement of copyright laws, and the development of technological solutions to combat illegal content distribution. Furthermore, raising awareness among consumers about the negative impacts of piracy is equally important.
By understanding the complexities involved in accessing a Raspberry Pi remotely and by considering the ethical considerations surrounding online content distribution, we gain a more holistic view of the interconnected technological landscape of the 21st century.